IAM Responsibilities Within Operational Roles
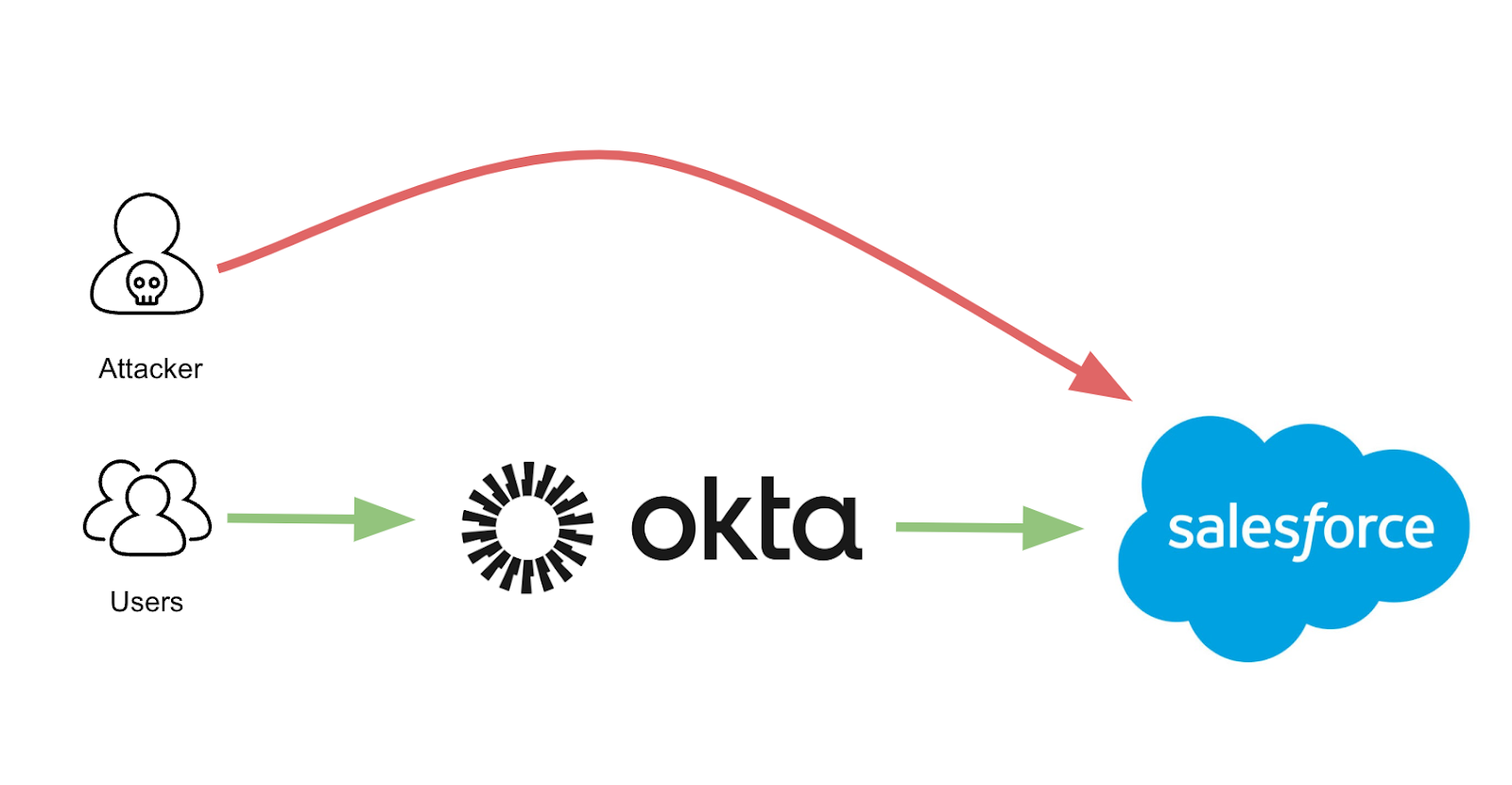
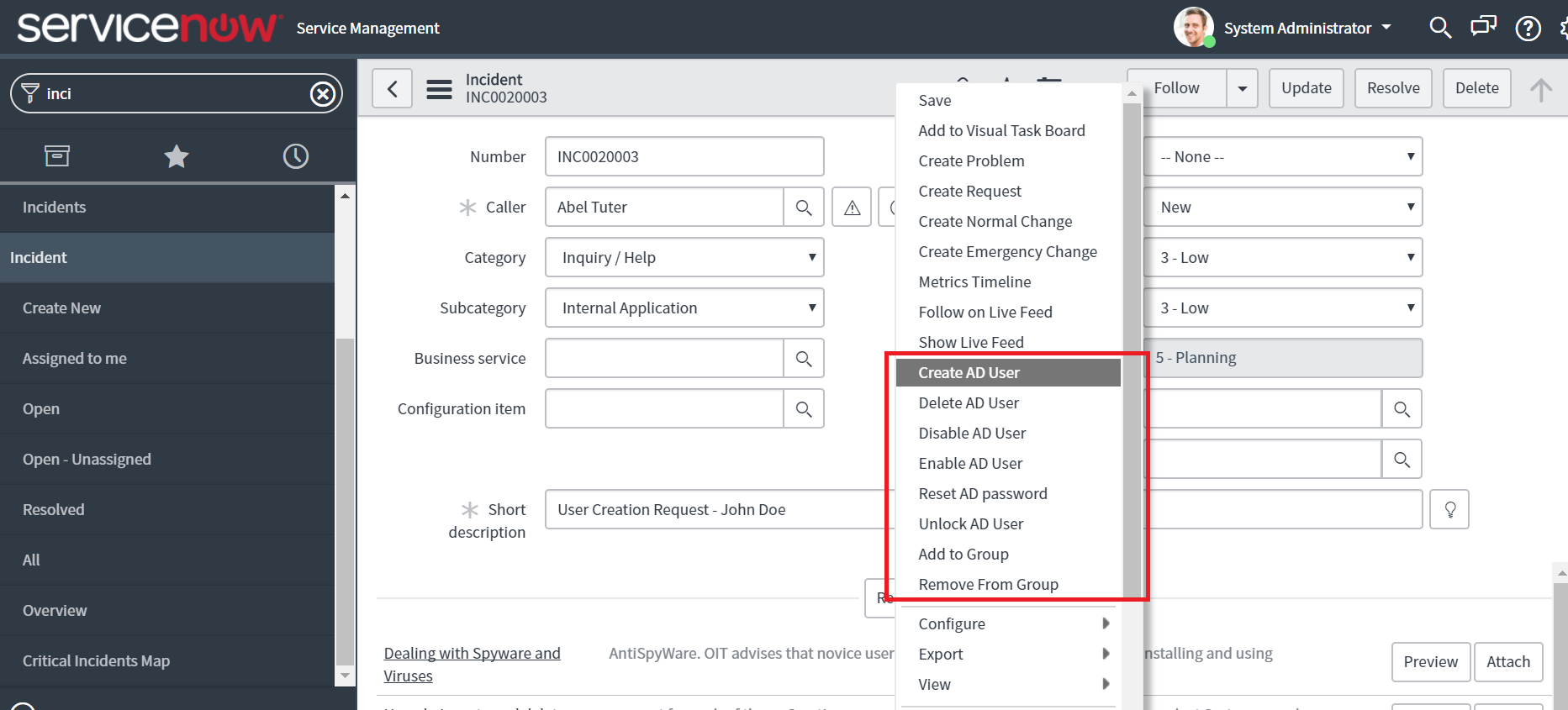
Identity and access management isn't just my career goal—it's work I'm already performing. Within IT infrastructure and support roles, I handle provisioning, access troubleshooting, authentication issues, and governance tasks daily. Every locked account is an authentication investigation. Every permission escalation becomes an RBAC discussion.
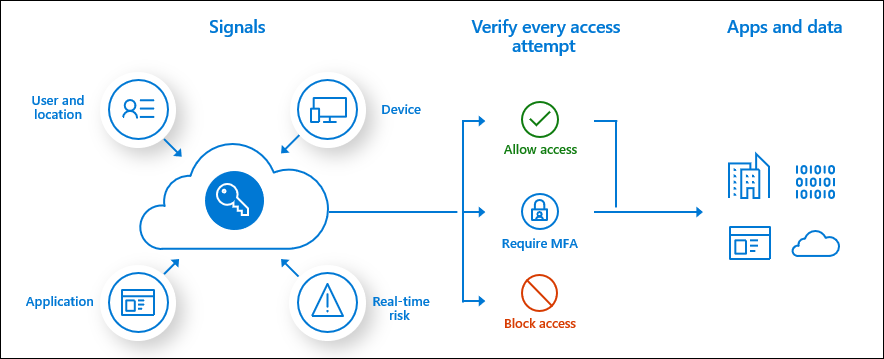
My hands-on experience with Active Directory, Entra ID, Okta, and enterprise access workflows gives me operational context that pure lab work can't replicate. Now I'm formalizing those patterns through structured labs—SCIM provisioning, conditional access policies, PAM workflows—to deepen engineering capabilities while maintaining real-world grounding.